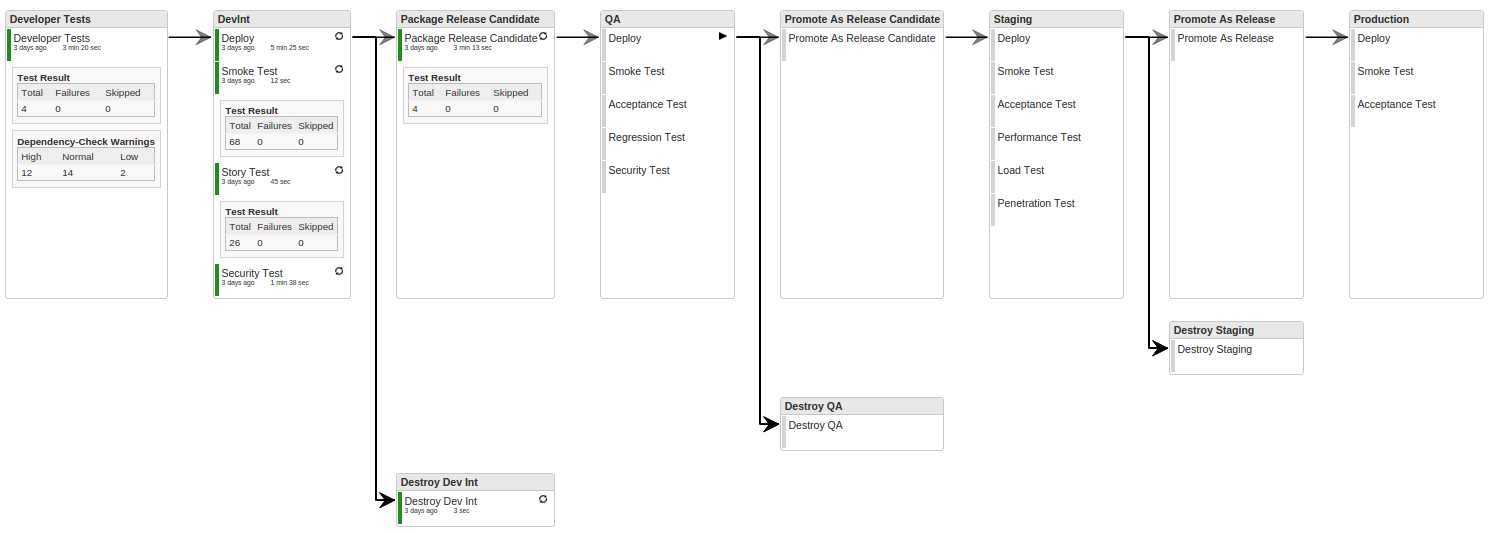
Many organizations we work with have some understanding of front-end testing using tools like Selenium. However, they struggle to prioritize, understand or properly implement security scanning in their Agile/DevOps Development process. One of the easiest ways to implement security testing with little to no additional effort is to use OWASP Zed Attack Proxy in conjunction […]