Accelerate secure software delivery with proactive and integrated application security practices
Application Security is not a single tool or tactic. AppSec is a combination of effective and efficient security practices, teams, and tooling to enable business success.
Coveros provides skilled professionals, expert guidance, and practical technology solutions to support your security efforts.

Application Security is a business enabler
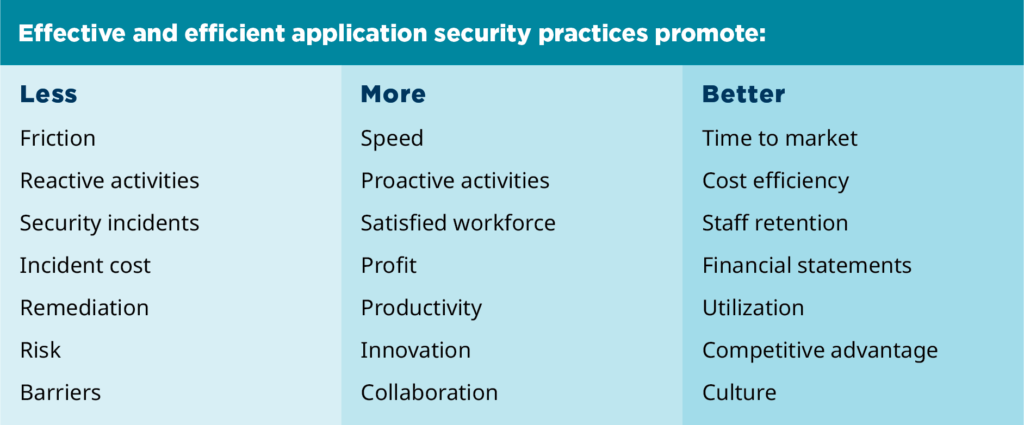
Effective and efficient application security practices promote:
Coveros Application Security Signature Services

DevSecOps Services
DevSecOps is the integration of security staff, practices, and automation into cross-function DevOps teams and associated delivery pipelines. In today’s DevOps world of continuous everything, application security must speed up to keep up with the pace of business. But while speed is important, your intellectual property, clients’ privacy, and the services your applications provide need to be protected in the process.
Coveros has significant DevSecOps experience, helping organizations both implement DevOps with security in mind and integrate security capabilities into your existing DevOps process. Our security experts can help you both define and implement a DevSecOps program and find threats and vulnerabilities in your code using threat modeling, static code analysis, dynamic security testing, software component analysis, and penetration testing.
Security Assessments & Remediation
Assessing and remediating software vulnerabilities is an essential step in building secure applications. Unfortunately, many organizations wait until the last minute to assess their application security posture. Not only is late lifecycle security analysis not an effective mechanism for identifying vulnerabilities but it leaves no time to correct any of the identified issues. DevSecOps strives to correct this.
At Coveros, we provide full lifecycle analysis of your software development artifacts as well as remediation services to correct the problems we find. Security analysis typically include a combination of assurance techniques based upon where you are in the development cycle and the criticality of your applications:
- Misuse/abuse analysis of requirements
- Threat modeling and architectural risk analysis
- Secure design reviews
- Secure code reviews
- Review of security testing capabilities
- Red teaming / penetration testing
Remediation services focus on modifying your design and code base to mitigate vulnerabilities and help you deliver secure software faster. Our DevSecOps engineers are all software engineers by training who are capable of remediating code in a variety of languages and for most common platforms.
Secure Agile Development
When agile methods are used with security-critical applications, it is essential that software security best practices be built into your process. Coveros has pioneered a secure agile development process, called SecureAgile, that integrates software security practices into a Scrum and XP-based agile process.
Coveros Secure Agile Process:
Our Secure Agile Development service can be delivered in a variety of models depending upon your needs:
- Outsourced Development – Coveros designs, implements, tests, and delivers secure code
- Blended Teams – Our security engineers pair and work with your teams to deliver secure applications while mentoring your staff on secure development approaches
- Application Security Program – Security experts from Coveros work to put in place a Secure Agile framework to allow your development teams to build secure software
Integrating Security Tools into DevOps
Continuous security is a key component of building releasable software on a frequent basis. Coveros has over a decade’s worth experience integrating security tools into continuous integration and continuous delivery processes.
Our experienced DevSecOps engineers can assist with integrating security tools into your DevOps process including:
- Lightweight static code analysis during build check-ins performed during continuous integration
- Robust static code analysis (IAST) into nightly regression testing processes and QA environments
- Network and passive vulnerability analysis to detect issues in production-like environments
- Dynamic security testing into continuous integration and continuous delivery processes
- Software component analysis to detect vulnerable open source frameworks and libraries
- Security monitoring to detect attacks in real-time
Security Testing
Regardless of your efforts to build security into your applications, security testing continues to be a necessary part of any application security program. Design flaws, implementation bugs and misconfiguration of environments or networks can all result in vulnerabilities that must be identified prior to release. At Coveros, our security testing experience includes both manual and automated analysis of applications across the full spectrum of possible vulnerabilities. Some of the many security testing services we offer include:
- Risk-based security testing – Assures identified threats and risks are not able to compromise your systems or access sensitive customer data
- Security testing of controls – Guarantees all integrated security controls (e.g. authentication, authorization, logging) have been securely integrated
- Open source libraries – Validates that existing open source frameworks and libraries have no known vulnerabilities
- System security testing – Tests associated networks, platforms, and 3rd party integrations to assure the application is secure within its environment
DevSecOps Jump-Starts
SecureCI Jump-Start – To help those just beginning their DevSecOps journey, Coveros has released SecureCI™, an open source DevOps toolstack with integrated security analysis. The SecureCI Jump-Start program helps organizations maximize the impact that continuous integration and the use of SecureCI™ have on the software development process. This week-long service provides on-site support from a Coveros continuous integration consultant who will help with installation, configuration, automation, app security analysis tools, and all other aspects of the SecureCI solution. For more details on this program, see our detailed Jump-Start information.



