Prevention and detection are key tools in medicine.
Stopping a serious illness from growing worse is easier when doctors find it early, because it usually saves the money, time, and physical and emotional stress that comes with prolonged illness and aggressive treatment.
There’s no comparison between the personal impact a serious illness has on patients and their loved ones and the impact of security vulnerabilities on software applications. But applying this early detection and prevention approach to AppSec can save your organization from the costs and embarrassment that come with large-scale security breaches.
Unfortunately, AppSec is still often an afterthought in the development lifecycle–and an expensive one.
The increasing costs of security vulnerabilities
According to the IBM Cost of a Data Breach 2023 Report, the global average total cost of a data breach is $4.45 million. Unfortunately, the average cost of a data breach in the United States is $5 million more at $9.44 million. For specific industries, such as healthcare, the average cost is higher than $10 million.
In other words: Security vulnerabilities are expensive.
The good news? Security vulnerabilities are much less expensive when they’re found early in the software development lifecycle.
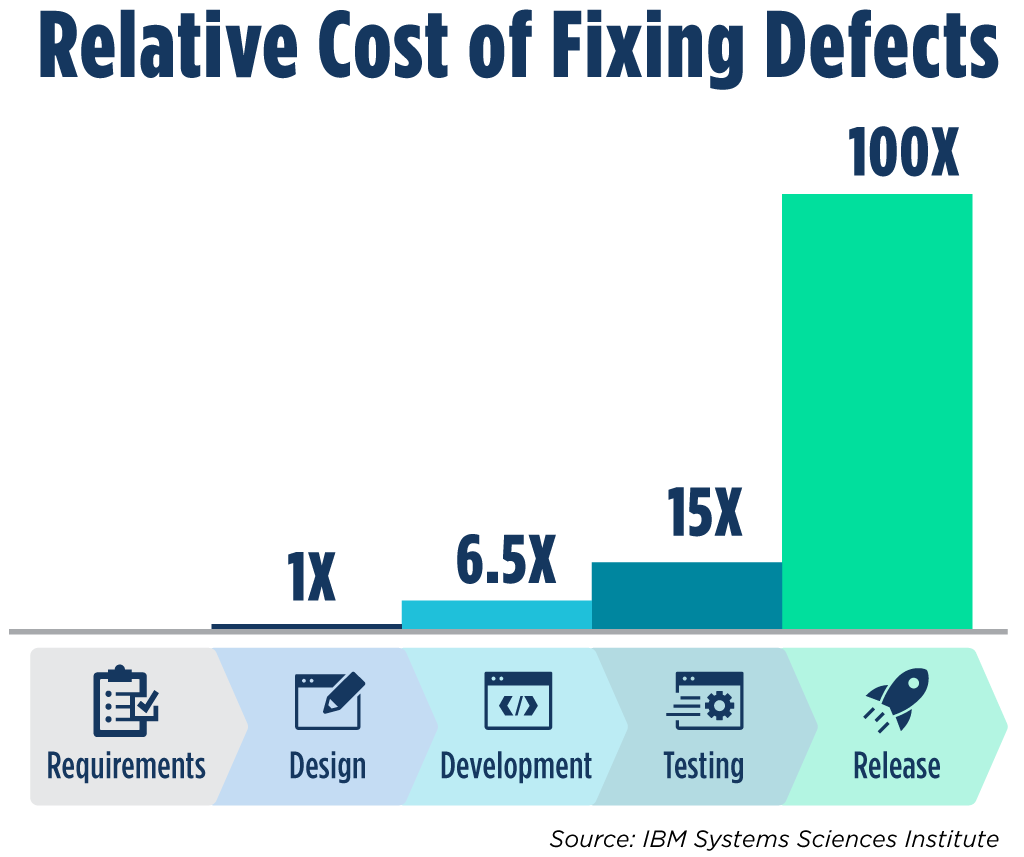
An estimate from the IBM Systems Sciences Institute shows the increasing cost of fixing security defects at each stage of the SDLC. This estimate shows that security defects found at the testing stage are 15 times more expensive to fix than those found in the requirements stage. Even worse, those defects found in the release phase are 100x more costly than those found in the requirements stage.
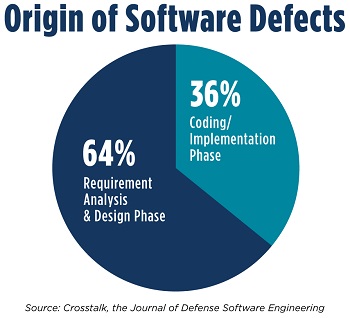
Even better news: The majority of security defects actually start in the requirements and design phase of the lifecycle. According to CrossTalk: The Journal of Defense Software Engineering, two-thirds of software defects have origins in these first two phases of the SDLC, while only one-third start in the coding and implementation phase.
If we examine these trends, the bottom line becomes pretty clear. The earlier in the SDLC we detect security vulnerabilities, the cheaper and quicker it is to fix the problem. In addition, having the same developer who inadvertently created the vulnerability fix it during development decreases the likelihood they will make the same mistake.
Assessing your security posture with OWASP SAMM
One of the most common questions we receive when we consult with organizations struggling with AppSec improvement is “Where do we start?”
For most organizations, the best first step in ensuring security vulnerabilities are caught early–or prevented before they even happen–is assessing your current AppSec culture, processes, and strategies.
This is where an OWASP SAMM can be a huge help.
An Open Web Application Security Project (OWASP) Software Assurance Maturity Model (SAMM) is just a fancy title for a comprehensive assessment of your SDLC’s current security stance.
The mission of an OWASP SAMM assessment is to provide an effective and measurable way to analyze and improve your software security posture. Since this framework was built by OWASP, it is a reflection of what industry best practices are and an accepted measuring stick, rather than a theoretical framework based on a vendor product.
SAMM is a framework to help organizations assess, formulate, and implement a strategy for software security that can be integrated into their existing SDLC. It supports the complete software lifecycle and is technology and process agnostic. Because there is no one-size-fits-all approach to security, SAMM is intentionally built to be iterative and risk-driven. The outcome of any SAMM is a full analysis of the maturity of your organization’s current application security, along with a roadmap for improvement, traditionally this is best done by experts with an objective and non-biased view.
How OWASP SAMM assessments work
While every OWASP SAMM is specialized for each specific organization, the core of the assessment is an evaluation of your current security posture along 15 security practices.
Those practices are divided among five focus areas:
Experts delivering OWASP SAMM assessments first gather as much information as possible through interviews, data, and other artifacts. Once this initial discovery phase is complete, experts evaluate the maturity of your organization along each of the security practices and identify major gaps, problem areas, and points for improvement.
Next, experts provide a roadmap with organizational and technology recommendations along with estimated time of implementation. By advancing these capabilities, your organization will be able to build a scalable Application Security program that improves your security posture.
When done right, OWASP SAMM assessments should provide a high-level playbook that you can start to implement to ensure you’re detecting and preventing security vulnerabilities in your SDLC. Think of it as your own AppSec health plan.
The importance of an independent evaluation
It may be tempting to perform your own internal OWASP SAMM assessment, but that’s a mistake. The most important part of a quality evaluation is the independence of the evaluators.
In performing OWASP SAMMs for companies across the country, we’ve found it’s often easier for teams to talk to outside, neutral experts rather than communicate about issues internally. Independent evaluators apply an unbiased, fact-based analysis to the challenges facing an organization, rather than the often emotional, biased approach applied by internal teams. For this reason, the independence of evaluators is vital to ensuring confidential, but open and honest conversations that lead to real discovery and improvement.
Just as you’d want a doctor to be as unbiased and upfront as possible to ensure the proper treatment for medical challenges, you should also want that same independent outlook in assessing your security posture.
Ready to take a look under the hood of your AppSec maturity? Our team of experts has conducted dozens of assessments for organizations of all sizes and industries. We’d love to talk about how we can apply an independent view to your security struggles. Talk to an expert today.

Application Security Consultant