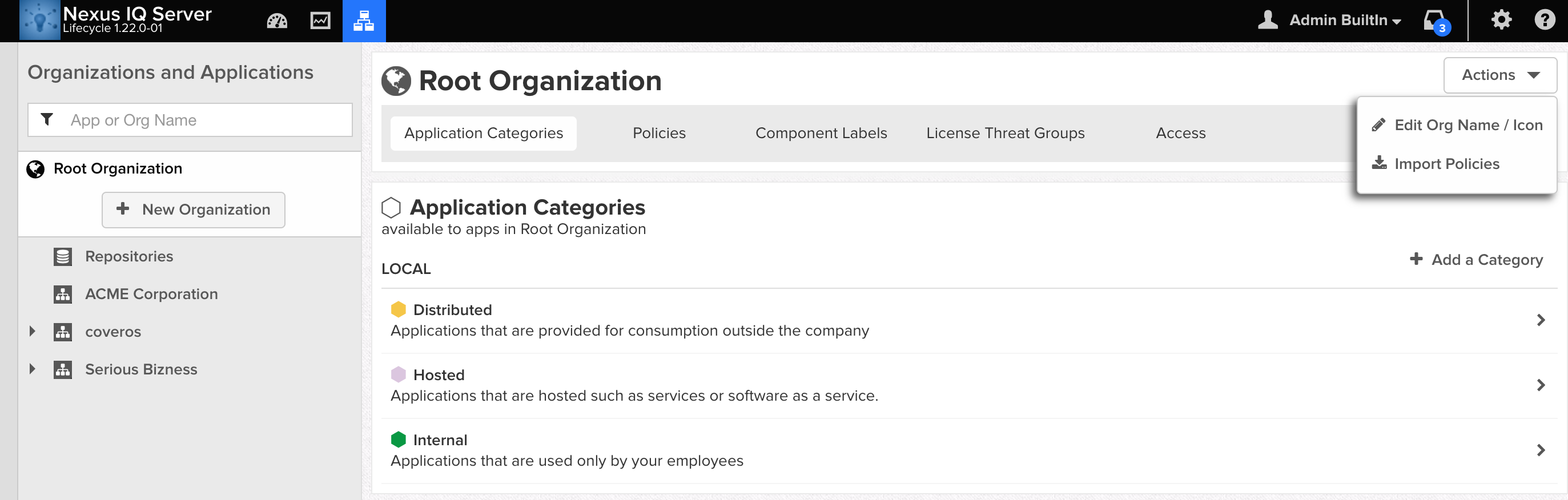
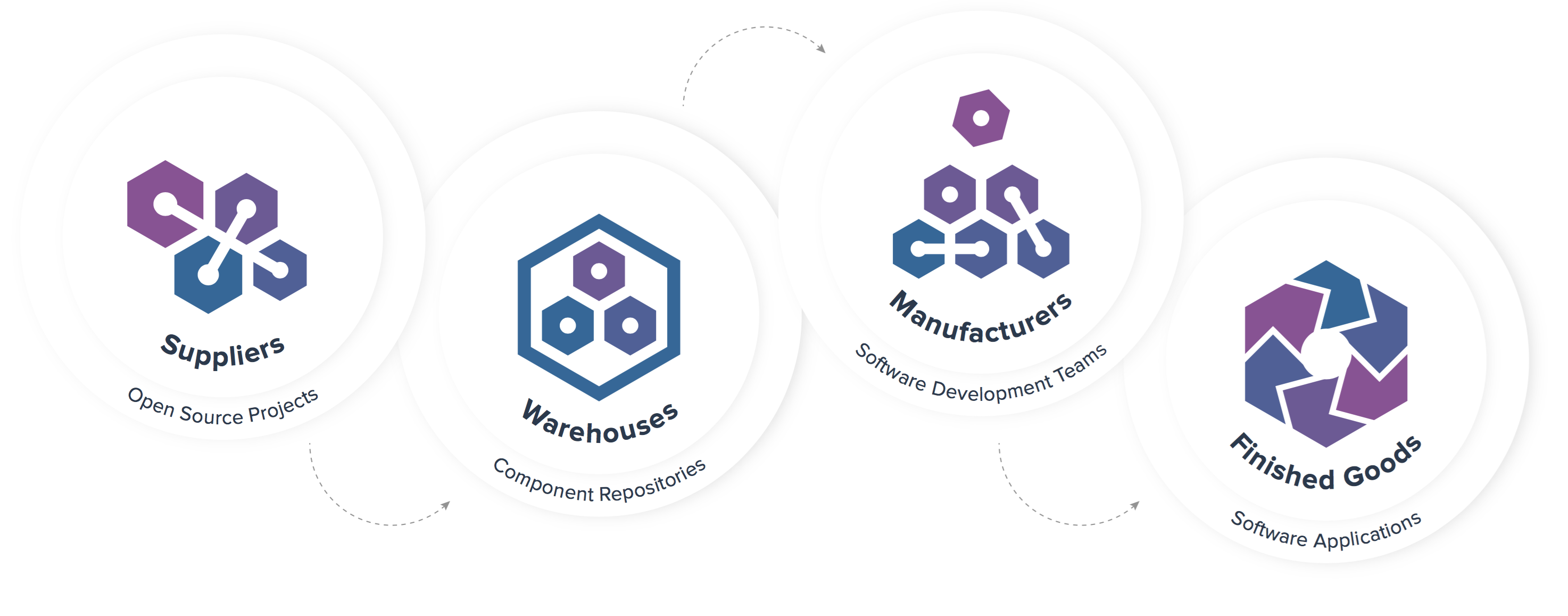
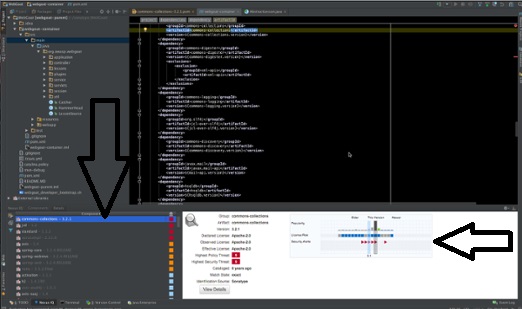
Mobile application development has been on the rise lately because of the convenience mobile apps have to offer. Despite the occurrence of security breaches performed on mobile devices recently, security testing is not as emphasized as other forms of quality testing measures such as user acceptance or functional testing. Just last year, hackers in China […]