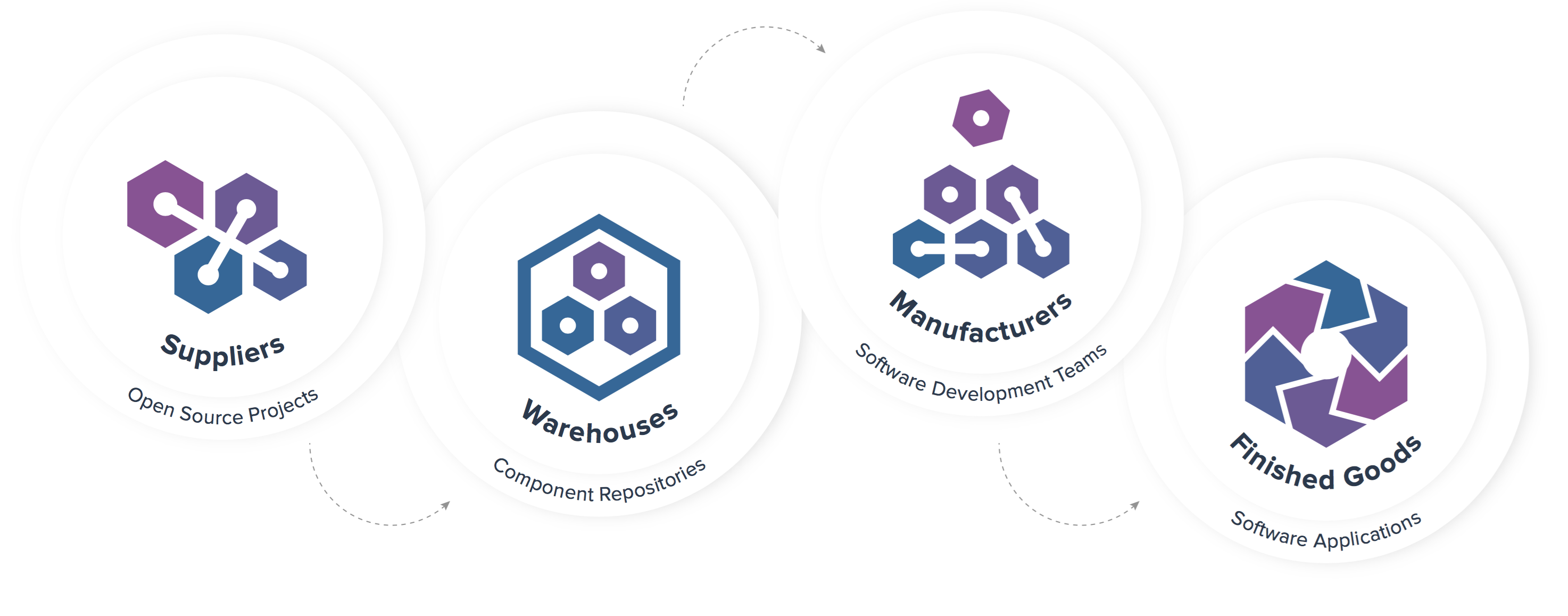
By now, most organizations have heard of DevOps, and many have begun to adopt DevOps practices as a key enabler of software delivery. Organizations that employ an agile approach find DevOps practices a natural extension, and DevOps truly enables agile practices to flourish. Organizations typically start with implementing continuous integration, test-driven development, and test automation […]