Knowing where to start in the penetration testing world is very difficult and largely inconsistent. With so many options and tools available simply kicking off a scan of the network can require a considerable time investment. That is even truer in the relatively new world of mobile testing.
Please only use the tools and methods discussed on systems that you own and have the right to access.
I have researched countless tools to solve specific problems that resulted in needing significant configurations for use or they did not work at all. Worse these tools have a common issue of being laden with extra software (read as: adware).
In these cases it is ideal to have a starting point, a Swiss army knife of tools that are readily available. For penetration testing, the gold standard is Kali, formerly BackTrack. The Kali virtual machine comes packaged with enough tools to perform a full penetration test and is configured to work with generally little customization. However, out of the box Kali cannot test mobile devices and their applications to the extent that is often required.
Enter AppUse created by AppSec-Labs.
AppUse can arguably be described as the Kali of the mobile testing world. This tool is not new, but the latest upgrade has considerably added to its capabilities.
The downloadable virtual machine comes bundled with mobile testing tools to run against both device operating systems and applications run on those devices.
Its dashboard, shown below, is user-friendly with a UI containing point and click options.
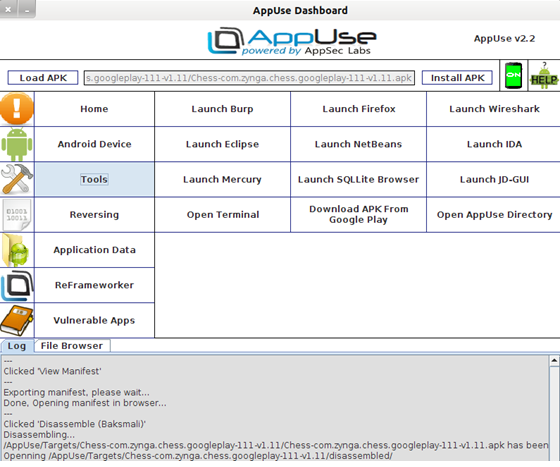
All of these tools are installed and customized such that their executables are included in the run PATH making them conveniently capable of being called on the command line for added control. These tools include, but are not limited to:
JD-gui – Helps reverse engineer and translate Android application packages (.apk files) into a more readable java format for static analysis
SQLLite Browser – Reads databases extracted from devices or local instances
Reassemble (Smali) – Bundles a deconstructed and modified application into an installable .apk format
Burp Suite – A proxy tool that also can spider and scan a target application or website
Interestingly, by setting up Burp as a proxy, I was able to identify certain instances of PII unexpectedly leaking from my devices.
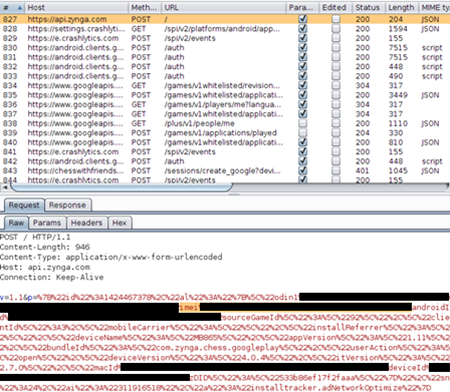
Within the registration request of Chess with Friends Free, PII in the form of my smart phone’s International Mobile Station Equipment Identity (imei) and MAC address were sent to Zynga. This information is continually sent via POST requests over regular intervals during the application’s usage. In the Pandora app, my full name associated with my Facebook account was sent despite Facebook being turned off under my settings in Manage External Services.
In both cases, my information was delivered in plain text such that if my connection were compromised, a malicious Access Point could trivially obtain all of this personal information.
Other Services:
Open ADB shell – Initiates a direct connection to an attached physical or emulated device
Root Device – Attempts to obtain root on an attached device
Launch Emulator – It is not always possible to root the target with the Root Device easy button. In many cases it may not be possible to root the target device within a reasonable amount of time. Therefore, AppUse comes with an emulator service, provided by Android SDK, which has root privileges to give a full scope of a chosen mobile device or installed application.
Screenshot – Displays the device’s screen for artifact gathering or logging
GoatDroid – 1 of 4 vulnerable apps bundled with AppUse to teach users how to apply the tools and learn their expected behaviors
View Manifest – Extracts the permissions of a given app from the .apk install file
Although the permissions requested by an app are presented at installation, it is often glanced over without extracting the meaning as users do not care what they are allowing so long as they can play a given game. Moreover, requesting permissions without context can lead to confusion. For example, using View Manifest on 2 similar Chess apps, I can observe that Zynga’s Chess with Friends Free app requires permissions to access the device’s INTERNET, ACCESS_WIFI_STATE, ACCESS_NETWORK_STATE, READ_PHONE_STATE, WRITE_EXTERNAL_STORAGE, VIBRATE, READ_CONTACTS, com.android.vending.BILLING, com.google.android.c2dm.permission.RECEIVE, and com.zynga.chess.googleplay.permission.C2D_MESSAGE. On the other hand, AI Factory’s Chess Free seems benign by only requiring permission be granted for INTERNET, ACCESS_NETWORK_STATE, and WRITE_EXTERNAL_STORAGE. One of these apps arguably is asking for more permissions than it should.
A glaring caveat with this framework is that the latest version of AppUse, 2.2, uses a 32 bit kernel. However, the Android SDK considers this deprecated to the point that it alerts the user directly with a popup that temporarily halts the application. In fact, special libraries were needed to connect my test devices through the android debug bridge.
Upgrading the native sdk libraries resulted in making the entire vm no longer compatible with the test devices.
That being said, I am using AppUse as a blueprint for tools to import into a custom testing framework I am currently building.
AppUse sets great groundwork and is an excellent first step into the world of mobile testing, for both penetration testers and developers. Hopefully future updates will become compatible with Android development.
In following posts, I will be demonstrating the installations and customized configurations to test both apps and mobile OS using these tools.



